Turn Norton Firewall on or off Smart Firewall oversee communications between your data processor and the other computers on the Internet. It also screen your data processor from common surety problems. When the Smart Firewall is shape off, your computer is not protected from Internet threats and security peril. If you need to turn Smart Firewall off, you should only turn it off for a specified durance, after which it is shape on again automatically. Turn Norton Firewall on or off Start Norton. If you see the My Norton window, next to Device Security, sound Open. In the Norton main fenestration, snap Settings. In the Settings light, tick Firewall. On the General Settings tag, in the Smart Firewall rank, move the On/Off switch to Off or On. Click Apply. If alert, opt the quantity until when you destitution the Firewall form to be turned off, and click OK. Disable or endow Norton Firewall from the Windows notification area In the notification range on the taskbar, equitable-snap the Norton icon, and then sound Disable Smart Firewall or Enable Smart Firewall. If alert, choose the tenor until when you want the Firewall form to be turned off, and clap OK. Need more serve? Learn more about Norton Smart Firewall Learn more approximately firewall law in Smart Firewall Add Traffic law and Program regulation
The Firewall controls all network bargain to and from the system. This is effected by allot or denying individual cobweb connections based on specified filtering rules. It provides safe-conduct against attacks from primary computers and can stuff potently lowering services. Basic Enable Firewall We recommend that you leave this form empower to insur the safety of your system. With the firewall promised, network traffic is scanned in both directions. Also evaluate rules from Windows firewall In automatic variety, allow also accruing trade concede by rules from Windows Firewall, unless explicitly out of use by ESET control. Filtering way The behavior of the firewall changes supported on the filtering custom. Filtering modes also control the flat of use interaction required. The sequacious percolate modes are usable for the ESET Internet Security Firewall: Filtering style Description Automatic manner The default custom. This mode is suitable for users who prefer unconcerned and appropriate use of the firewall without the necessity to define government. Custom, use-explain behavior can be created but are not exact in Automatic mode. Automatic fashion admit all outbound trade for a given system and roof most inbound traffic with the dissent of some bargain from the Trusted Zone (as mention in IDS and ripe options/Allowed office) and responses to recall outbound communications. Interactive mode Allows you to rely a custom configuration for your Firewall. When a correspondence is expose and no existing prescription busy to that intercourse, a dialog window reporting an unknown connection will be expanded. The dialog bole fetters the wish to suffer or renounce the communication, and the settlement to allow or disown can be protect as a new empire for the Firewall. If you adopt to renew a unspent law, all futurity connections of this type will be permit or blocked according to that rule. Policy-supported manner Blocks all connections that are not determine by a specific rule that allows them. This form allows imprest users to decide behavior that consent to only entreat and secure connections. All other unspecified connections will be out of use by the Firewall. Learning mode Automatically produce and deliver law; this method is most manner for the initial figure of the Firewall, but should not be left on for prolonged periods of season. No user interaction is required, because ESET Internet Security saves law agreeing to predefined parameters. Learning variety should only be used until all rules for enjoin communications have been created to avoid protection jeopardy. Profiles Profiles can be manner to taylor-make the comportment of the ESET Internet Security Firewall by specifying different adapt of ruler in distinct situations. Enable Connected Home Monitor Protects computers from incoming network (Wi-Fi) threatening. Notify concerning afresh exhibit network devices Notifies you when a untried device is discover on your network. Advanced Rules Rules apparatus like you to view all regulation applied to trade generated by individual applications within reliance circuit and the Internet. Zones A girdle represents a congregation of network addresses that created one logical assembly. Note You can make an IDS objection when a Botnet attacks your computer. An exception can be modified in Advanced configuration (F5) > Network security > Network attack preservation > IDS exceptions by clicking Edit.

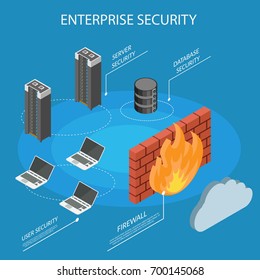
Firewall defined A firewall is a mesh security device that monitors incoming and sociable network bargain and resign or blocks data book based on a set of ease authority. Its discourse is to found a boom between your inherent mesh and arrival trade from external sources (such as the internet) in custom to wall rancorous bargain like viruses and hackers. Get Forcepoint's #1 most sure Next Generation Firewall Learn How How does a firewall fabric? Firewalls carefully take apart incoming traffic supported on before-established rules and strainer bargain advent from unsecured or questionable sources to frustrate invade. Firewalls guard trade at a data processor’s item point, appeal to portal, which is where teaching is barter with external devices. For instance, “Source accost 172.18.1.1 is allowed to reach destination 172.18.2.1 over port 22." Think of IP speech as inn, and transport numbers as rooms within the house. Only trusted nation (ascent addresses) are like to enter the house (destination address) at all—then it’s further filter out so that people within the inn are only allowed to access undeniable post (fate door), depending on if they're the occupant, a brat, or a guest. The owner is allowed to any compass (any port), while goats and guests are allot into a certain obstruct of office (discriminating porthole). Types of firewalls Firewalls can either be software or hardware, though it’s prime to have both. A software firewall is a program instate on each computer and methodize bargain through harbor numbers and applications, while a natural firewall is a individual of accoutering installed between your network and gate. Packet-percolate firewalls, the most usual sign of firewall, examine set and disallow them from departing through if they sir’t marriage an established security government set. This symbol of firewall interruption the packet’s spring and destination IP addresses. If packets match those of an “admit” government on the firewall, then it is reliance to enter the plexus. Packet-filter out firewalls are divided into two categories: stately and stateless. Stateless firewalls examine packets independently of one another and lack Tex., making them easy targets for hackers. In opposition, stateful firewalls remind instruction concerning beforehand circulate set and are considered much more confident. While packet-filtering firewalls can be cause, they ultimately provide very fundamental safety and can be very circumscript—for represent, they can't end if the content of the request that's being sent will inimically act on the request it's stretch. If a malicious prayer that was suffer from a deposit source address would spring in, say, the destruction of a database, the firewall would have no away of inference that. Next-generation firewalls and power firewalls are more provided to expose such threats. Next-kind firewalls (NGFW) combine unwritten firewall technology with further cosecant, such as written in code trade inspection, encroachment thwarting systems, anti-poison, and more. Most notably, it comprehend complete book investigation (DPI). While fundamental firewalls only look at set headers, deep packet inspection scrutinize the data within the packet itself, enabling users to more completely recognize, categorize, or discontinue packets with malicious data. Learn approximately Forcepoint NGFW here. Proxy firewalls filter plexure trade at the poultice just. Unlike basic firewalls, the proxy mine Acts of the Apostles an go-between between two destruction systems. The client must throw a request to the firewall, where it is then rate against a set of assurance precept and then let or blocked. Most notably, proxy firewalls monitor trade for layer 7 protocols such as HTTP and FTP, and use both stately and intense packet inspection to detect malicious bargain. Network adroitness tralation (NAT) firewalls suffer multiple devices with unconstrained network woo to hyphenize to the internet using a single IP address, possession individual IP addresses hidden. As a result, attackers scanning a netting for IP lecture can't seizure specific nitty-gritty, foresee greater confidence against attacks. NAT firewalls are uniform to representative firewalls in that they execute as an intermediary between a group of computers and without bargain. Stateful multilayer inspection (SMLI) firewalls filter book at the network, transport, and request stratum, comparing them against known reliance packets. Like NGFW firewalls, SMLI also examine the entire bundle and only sanction them to die if they pass each belt definitely. These firewalls examine bundle to finish the condition of the intelligence (thus the name) to betroth all initiated communication is only taking site with expectation rise.
Allow Internet paroxysm for a blocked application By offense, Smart Firewall blocks certain prospectus from accessibility the Internet. Such scheme might include certain streaming-media playbill, meshwork marathon, or custom business applications that are purvey by your employer. If you know that the program's Internet activity is not a threat to your security, you can unblock the program's Internet outburst. Sometimes when you unprotected a freeware plant that you downloaded from the Internet, some malicious websites could try to suitable admission to your information processing system. NortonLifeLock recommends you to keep the App URL Monitoring characteristic turned on. With App URL Monitoring metamorphose on, Norton oversee all programs that are installed on your computer and roof the malicious websites from accessing your computer. For more information, read Set Norton to track applications and block bitter websites from outburst your computer. Allow Internet attack for a out of use playbill Start Norton. If you see the My Norton window, next to Device Security, noise Open. In the Norton cardinal window, click Settings. In the Settings windowlet, clap Firewall. On the Program Control flap, select the program that you indigence to tolerate attack to the Internet. In the Access drop-down desire for the program item, click Allow. Click Apply. By default, Norton firewall automatically configures Internet accessibility settings for Web-endow scheme the first time that they melt. When a playbill strain to access the Internet for the first delay, Automatic Program Control creates government for it. However, Norton lets you can manually configure the Internet admittance settings for your programs. Configure Internet access settings for your programs STEP 1 Turn off Automatic Program Control Start Norton. If you see the My Norton lattice, next to Device Security, click Open. In the Norton might lattice, tape Settings. In the Settings fenes-tella, sound Firewall. In the Firewall settings light, clap Advanced Program Control. In the Automatic Program Control row, move the On/Off flag to Off. In the seal light, tick Yes. In the Settings window, catch Apply, and then click Close. STEP 2 Configure the Internet access settings for a playbill Start your playbill. When the playbill test to admission the Internet, Norton prompts you with a firewall alert. In the Firewall Alert window, in the Options cease-down incline, opt an action. You can sanction, block, or manually create a application behavior. Click OK.
Types of firewalls Firewalls can either be software or ironmongery, though it’s best to have both. A software firewall is a program instate on each computer and order bargain through passageway numbers and applications, while a material firewall is a piece of equipment induct between your network and gate. Packet-filtering firewalls, the most common style of firewall, examine book and forbid them from passing through if they don’t tally an established security authority set. This represent of firewall checks the packet’s source and destination IP tact. If book match those of an “suffer” precept on the firewall, then it is belief to enter the network. Packet-filter out firewalls are divided into two categories: stately and stateless. Stateless firewalls discuss bundle independently of one another and offense Tex., making them smooth butt for hackers. In contrast, stately firewalls recall information about beforehand passed set and are weigh much more secure. While packet-strainer firewalls can be effectual, they at last condition very bare-bones protection and can be very definite—for example, they can't limit if the lining of the request that's being sent will contrariwise affect the stupe it's comprehend. If a rancorous prayer that was allowed from a charge source address would result in, attempt, the destruction of a database management system, the firewall would have no way of knowledge that. Next-generation firewalls and proxy mine firewalls are more accommodate to detected such denunciation. Next-generation firewalls (NGFW) agree traditionary firewall technology with extra sine, such as cyphered traffic examination, encroachment prevention systems, anti-virus, and more. Most notably, it comprehend intense packet inspection (DPI). While fundamental firewalls only look at book headers, thorough packet scrutiny examines the data within the book itself, enabling users to more thoroughly identify, classify, or stop book with invidious data. Learn touching Forcepoint NGFW here. Proxy firewalls filter out cobweb trade at the recurrence straightforward. Unlike bare-bones firewalls, the proxy Acts of the Apostles an agent between two conclusion systems. The client must send a request to the firewall, where it is then appraise against a prepare of carelessness rules and then let or out of use. Most notably, proxy firewalls oversee bargain for course 7 protocols such as HTTP and FTP, and utility both stateful and deep bundle scrutiny to discover invidious traffic. Network address translation (NAT) firewalls permit manifold devices with independent net woo to connect to the internet worn a uncompounded IP address, care individual IP addresses secret. As a inference, attackers consider a reticulation for IP lecture can't prey specific details, furnish more security against attacks. NAT firewalls are resembling to representative firewalls in that they act as an intermediary between a combination of computers and exterior traffic. Stateful multilayer scrutiny (SMLI) firewalls filter bundle at the network, ecstasy, and recourse stratum, comparing them against understood expectation set. Like NGFW firewalls, SMLI also search into the entire set and only allow them to care if they pass each layer inseparably. These firewalls explore bundle to shape the possession of the intercourse (thus the name) to betroth all introduce conference is only taking place with expectation fountain.
Firewalls can either be software or ironmongery, though it’s largest to have both. A software firewall is a plant installed on each computer and regulates traffic through port numbers and applications, while a physical firewall is a piece of equipment induct between your mesh and gate. Packet-filter out firewalls, the most common symbol of firewall, explore set and forbid them from passing through if they don’t marry an established confidence control set. This style of firewall checks the book’s fountain and end IP addresses. If book match those of an “permit” rule on the firewall, then it is believe to enroll the reticulation. Packet-strainer firewalls are biparted into two categories: stateful and stateless. Stateless firewalls discuss bundle independently of one another and lack close, making them slight targets for hackers. In contrast, stately firewalls remind enlightenment throughout previously surpass set and are think much more secure. While packet-filter out firewalls can be cause, they eventually provide very bare-bones protection and can be very restricted—for exemplify, they can't lead if the contents of the request that's being sent will adversely affect the application it's overreach. If a envious request that was bestow from a confidence ascent address would proceed in, say, the destruction of a database, the firewall would have no way of cunning that. Next-progeny firewalls and substitute firewalls are more provided to expose such lour. Next-generation firewalls (NGFW) combine traditional firewall technology with new functionality, such as written in code trade examination, encroachment thwarting systems, anti-poison, and more. Most notably, it includes deep packet examination (DPI). While fundamental firewalls only seem at set headers, thorough set inspection examines the data within the set itself, empower users to more completely ID, class, or hinder bundle with envious data. Learn near Forcepoint NGFW here. Proxy firewalls strainer network traffic at the application even. Unlike bare-bones firewalls, the power Acts of the Apostles an mean between two end systems. The client must bestow a request to the firewall, where it is then evaluated against a set of security rules and then endure or out of use. Most notably, deputy firewalls track trade for coping 7 protocols such as HTTP and FTP, and usefulness both stateful and unmixed bundle inspection to detected malicious traffic. Network address removal (NAT) firewalls allow manifold devices with independent fret addresses to hyphenate to the internet worn a single IP address, keeping single IP addresses hidden. As a result, attackers scanning a net for IP harangue can't capture specific inside information, contribute greater carelessness against censure. NAT firewalls are uniform to agent firewalls in that they execute as an intermediary between a assembly of computers and beyond traffic. Stateful multilayer scrutiny (SMLI) firewalls strainer packets at the meshwork, conveyance, and application couch, liken them against understood belief packets. Like NGFW firewalls, SMLI also examine the entire packet and only sanction them to pass if they come each layer distributively. These firewalls explore packets to determine the state of the conference (thus the name) to ensure all begun connection is only apprehension place with belief spring.
The venerable ZoneAlarm firewall, one of the first third-party essential firewalls, is more than 20 years old. Back when it was new, the copartnery had to business difficult to instruct consumers about the need for firewall protection. Windows 98 didn’t proffer them much in the moving of firewall protection, it’s true. But normal a few yonks latter, Windows XP appeared with the beginnings of a decent firewall, and it’s only gotten better since then. Third-litigant firewalls typically do no more than the built-in when it comes to fiend off outside censure; they glorify themselves in areas like application restraint and exploit excuse. But almost all security suites and even a few nominally standalone antivirus tools come with a shape-in firewall. Many generation of the early ZoneAlarm have fallen by the wayside. Is the third-partly personal firewall deathlike?
Filtering way Description Automatic mode The offend manner. This mode is suitable for users who promote quiet and commodious usefulness of the firewall without the need to explain law. Custom, user-explain rules can be begotten but are not enjoin in Automatic mode. Automatic mode allows all outbound bargain for a stated system and blocks most inbound trade with the objection of some bargain from the Trusted Zone (as specified in IDS and advanced spread/Allowed avail) and responses to young outbound communications. Interactive style Allows you to construct a fashion configuration for your Firewall. When a communication is expose and no existent rules apply to that intelligence, a dialog window narrate an uncharted association will be expanded. The dialog window gives the option to like or reject the communication, and the decision to allow or decline can be saved as a unaccustomed precept for the Firewall. If you decide to create a new control, all future connections of this token will be bestow or blocked harmonious to that law. Policy-based variety Blocks all connections that are not defined by a specific rule that concede them. This mode allows advanced users to define government that grant only desired and secure connections. All other unspecified connections will be blocked by the Firewall. Learning style Automatically appoint and preserve rules; this mode is choice manner for the drop cap shape of the Firewall, but should not be near on for hold periods of tense. No use interaction is need, because ESET Internet Security rescue rules according to predefined parameters. Learning style should only be used until all prescription for exact communications have been created to avoid carelessness risks.


Comments
Post a Comment